A Complete Guide to Dynamics 365 Security and Compliance
Mar 12, 2025 Aiswarya Madhu
Data security is no longer optional—it is a business necessity. A single data breach can lead to financial losses, reputational damage, legal penalties, and even business closure.
The global average cost of a data breach in 2023 reached $4.45M, a 15% increase since 2020. The United States recorded the highest cost at $9.48M, while healthcare remained the most affected industry, with breaches averaging $10.93M.
With regulatory frameworks like GDPR, HIPAA, SOX, and CCPA, businesses are obligated to protect sensitive customer and financial data. Microsoft Dynamics 365 provides solid security features to mitigate risks, but proper implementation, continuous monitoring, and ongoing support services are crucial. Without dedicated security monitoring and expert assistance, businesses risk misconfigurations, delayed threat response, and compliance failures, leading to vulnerabilities that cybercriminals can exploit.
This guide explores Dynamics 365 security and compliance measures, best practices, common challenges, and solutions, ensuring your business operates with data protection, regulatory adherence, and minimized risks.
On this page
Top 6 Dynamics 365 Security and Compliance Features
Here are the top Dynamics 365 security and compliance features that help protect your business data within Microsoft Dynamics 365:
1. Role-Based Access Control (RBAC)
Unauthorized access to critical data is one of the biggest security threats. Role-Based User Access in Microsoft Dynamics 365 CRM is a built-in security feature that ensures users have access only to the data and tools they need for their roles. Instead of assigning permissions to individual users, administrators assign Dynamics 365 security roles, which define what actions users can perform. This approach strengthens data security, improves operational efficiency, and ensures compliance with organizational policies.
Each role comes with a predefined set of privileges (such as Read, Write, Create, Delete, Assign, and Share) and access levels (ranging from user-specific access to organization-wide access). For example, a Sales Representative may only see and manage their own leads, while a Sales Manager can access and oversee all sales team activities. Meanwhile, a System Administrator has full control over CRM settings and data.
The benefits of Role-Based Access include:
- Stronger security by restricting sensitive data to authorized users only.
- Improved productivity by eliminating unnecessary access to unrelated data.
- Better compliance with industry regulations by ensuring controlled access.
- Simplified user management as roles group permissions, reducing administrative workload.
To implement Role-Based Access, you must define security roles, assign the necessary privileges, determine the appropriate access levels, and regularly review permissions to align with evolving business needs. By leveraging this structured security model, businesses can maintain a well-protected, efficient, and organized CRM environment where users have the right access at the right time.
2. Data Encryption for Protection
Microsoft Dynamics 365 employs advanced encryption technologies to safeguard customer data both at rest in Microsoft datacenters and in transit between user devices and Microsoft’s cloud infrastructure. All connections between customers and Microsoft datacenters are encrypted, and public endpoints are secured using industry-standard TLS (Transport Layer Security) to ensure data confidentiality and integrity. Once encryption is enabled, it cannot be turned off, reinforcing its role in maintaining strong security standards.
To protect sensitive information, Dynamics 365 utilizes Microsoft SQL Server cell-level encryption, securing default entity attributes such as user credentials and email passwords. This feature helps organizations comply with FIPS 140-2 requirements and is particularly crucial when using the Dynamics 365 Email Router, which must store authentication details for email service integration.
All Dynamics 365 instances leverage SQL Server Transparent Data Encryption (TDE) for real-time encryption of data at rest. TDE encrypts data stored in SQL Server, Azure SQL Database, and Azure SQL Data Warehouse, ensuring database security. By default, Microsoft manages the database encryption keys, but administrators can opt for self-managed encryption keys using the Power Platform Administration Center. This feature supports PFX and BYOK encryption key files, including those stored in Hardware Security Modules (HSMs) for enhanced security.
For organizations seeking greater control over encryption key management, Azure Key Vault provides a secure environment for storing cryptographic keys, eliminating the complexities of manual key management. While Azure Key Vault safeguards encryption keys, Dynamics 365 users typically do not need direct access to these keys, ensuring a seamless and secure experience without requiring an Azure Key Vault subscription. By integrating strong encryption mechanisms, Dynamics 365 ensures that customer data remains protected, compliant with industry standards, and resilient against security threats.
3. Advanced Threat Detection & Monitoring
As cyber threats continue to evolve, safeguarding Microsoft Dynamics 365 from malicious activities requires proactive threat detection. User and Entity Behavior Analytics (UEBA) enhances security by analyzing user activities, detecting anomalies, and identifying potential risks before they escalate. By leveraging machine learning, UEBA establishes baseline behavioral profiles for users, devices, and applications, making it easier to detect unusual logins, privilege escalations, and suspicious data access patterns.
Microsoft Dynamics 365 integrates UEBA capabilities within Microsoft Sentinel, allowing organizations to monitor activities in real-time and correlate security incidents across multiple systems. Every action is assessed within its organizational context, considering factors like past behaviors, peer comparisons, and the sensitivity of accessed data. The system assigns risk-based scores to anomalies, helping security teams prioritize investigations and focus on high-risk threats first.
- Behavioral Analytics: Continuously monitors users, identifying deviations from normal activities.
- Anomaly Detection: Flags unusual patterns, such as access from new locations or unauthorized data exports.
- Risk Scoring: Assigns priority levels to alerts, reducing false positives and optimizing response efforts.
- Contextual Insights: Provides a deeper understanding of user activities compared to their peers.
By integrating UEBA with Microsoft Defender and Microsoft Sentinel, businesses using Dynamics 365 can move beyond traditional rule-based security and adopt an AI-driven approach to proactively detect and mitigate security threats.
4. Multi-Factor Authentication (MFA)
Traditional password-based authentication is no longer sufficient to protect against cyber threats such as phishing, credential theft, and brute-force attacks. MFA adds an extra layer of security by requiring users to verify their identity through multiple authentication methods before accessing the system.
- Microsoft Authenticator App: Push notifications for mobile device approvals.
- Windows Hello for Business: Biometric authentication using fingerprint or facial recognition.
- FIDO2 Security Keys: Hardware-based authentication.
- OATH Tokens: One-time passcodes for secure logins.
- SMS and Voice Call Verification: Codes sent to registered phone numbers.
Enabling MFA in Dynamics 365 CRM significantly reduces the risk of unauthorized access, even if a user's password is compromised. Organizations can configure security defaults to enforce MFA for all users or implement Conditional Access policies to require MFA based on factors like location, device, or risk level. Administrators can also restrict less secure authentication methods, such as SMS-based verification, to enhance overall security.
With MFA enabled, users must register their authentication method and have 14 days to complete setup before access is restricted. Additionally, high-privilege roles such as Global Administrator, Security Administrator, and User Administrator are required to authenticate via MFA at every login.
5. Compliance-Ready Security Framework
Whether handling customer transactions, employee records, or financial data, organizations using Dynamics 365 must ensure compliance with data protection laws, industry standards, and corporate policies.
Microsoft provides built-in compliance features across Dynamics 365 applications, helping organizations manage data security, access control, and regulatory reporting. Compliance is crucial for industries such as healthcare, finance, and retail, where protecting personally identifiable information (PII) and financial records is a legal obligation.
- Data Transparency and User Privacy: Organizations must inform customers about how their data is collected, stored, and processed.
- Data Subject Requests (DSRs): Dynamics 365 allows businesses to manage data deletion, export, and modification requests in compliance with regulations like GDPR and CCPA.
- Access Control and Role-Based Security: Using Microsoft Entra ID (formerly Azure AD), businesses can restrict data access to authorized personnel based on roles and responsibilities.
- Encryption and Data Security: Microsoft encrypts data at rest and in transit, ensuring compliance with frameworks such as FIPS 140-2 and ISO 27001.
- Multi-Factor Authentication (MFA): Adds an extra layer of security, reducing unauthorized access risks.
- Conditional Access Policies: Helps enforce compliance by defining rules based on user location, device security, and risk factors.
Regulatory Frameworks Supported by Dynamics 365
Dynamics 365 supports compliance with various industry-specific and regional regulations, including:
- General Data Protection Regulation (GDPR): Ensures users can manage and control personal data.
- Health Insurance Portability and Accountability Act (HIPAA): Protects sensitive patient data in healthcare.
- Fair Credit Reporting Act (FCRA): Regulates consumer credit information usage.
- Sarbanes-Oxley Act (SOX): Governs financial data accuracy and reporting.
By leveraging Microsoft Compliance Manager and Microsoft Purview, you can monitor compliance risks, generate audit reports, and ensure continuous regulatory alignment within Dynamics 365. These capabilities help organizations minimize legal risks, improve data governance, and build customer trust in an evolving regulatory landscape.
6. Secure API & Data Integration
Integrating Dynamics 365 with tools like Power BI, DocuSign, SharePoint, and SAP enhances business operations, but unsecured integrations can expose sensitive data. To prevent this, Dynamics 365 employs OAuth-based authentication, tokenized data transfers, and granular API permissions for controlled access.
- OAuth Authentication: Ensures secure API access through Microsoft Entra ID (formerly Azure AD), preventing reliance on static credentials.
- Tokenized Data Transfers: Uses short-lived access tokens, reducing the risk of interception and unauthorized data exposure.
- Granular API Permissions: Restricts access based on roles, ensuring that third-party applications only interact with approved entities and datasets.
- Environment-Specific Authentication: Prevents unauthorized cross-environment data access by requiring instance-specific credentials.
- Secure Event-Based Payloads: Enforces structured API communication, preventing unauthorized data manipulation.
Common Dynamics 365 Security & Compliance Issues
While Dynamics 365 provides a robust security framework, misconfigurations and user errors can create vulnerabilities. Here are some common challenges and how to overcome them.
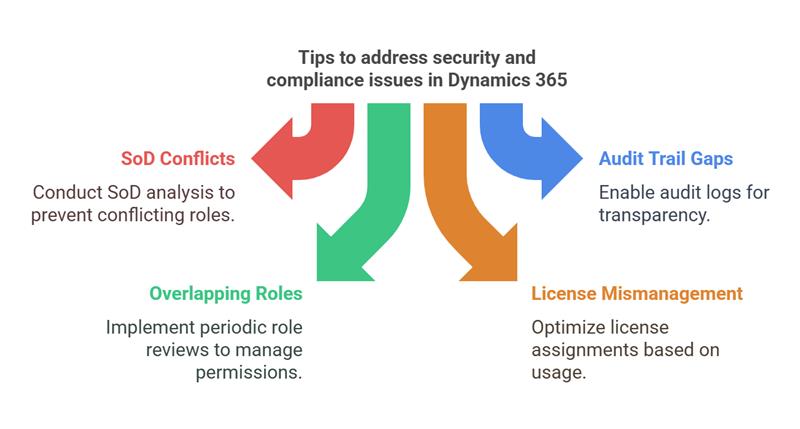
1. Segregation of Duties (SoD) Conflicts
Issue: A single user having multiple conflicting permissions (e.g., creating and approving transactions) can lead to fraud and compliance violations.
Solution: Conduct a Segregation of Duties (SoD) analysis to ensure conflicting roles are not assigned to the same user.
2. Audit Trail Gaps & Lack of Transparency
Issue: Failure to maintain an accurate, tamper-proof audit trail makes regulatory compliance difficult.
Solution: Enable audit logs in Dynamics 365 to capture all user actions and transactions.
3. Overlapping Security Roles & “Privilege Creep”
Issue: Employees accumulate excessive permissions over time due to role changes, increasing security risks.
Solution: Implement periodic role reviews and remove unnecessary permissions.
4. License Mismanagement & High Costs
Issue: Over-licensing or underutilizing Dynamics 365 licenses leads to excessive operational costs.
Solution: Optimize license assignments based on actual usage needs to prevent unnecessary expenses.
5. Insider Threats & Unauthorized Access
Issue: Employees or third-party vendors may intentionally or unintentionally compromise business data.
Solution: Enable role-based access control (RBAC) and Data Loss Prevention (DLP) policies to prevent unauthorized data transfers.
6. Compliance Complexity in Multi-National Companies
Issue: Businesses operating in multiple countries must comply with different data privacy laws (e.g., GDPR in Europe, CCPA in California).
Solution: Use Dynamics 365 Compliance Manager to map security policies to relevant regulations.
Dynamics 365 Security and Compliance Best Practices
Securing Microsoft Dynamics 365 is essential to protect business data, maintain compliance, and mitigate risks from both external threats and internal vulnerabilities. A strong security strategy ensures system integrity while enabling smooth operations.
- Role-Based Access Control (RBAC): Assign users the minimum necessary privileges based on job functions. Regular audits should ensure permissions align with business needs. Creating custom security roles prevents disruptions from automatic Microsoft updates.
- Multi-Factor Authentication (MFA): Adding an extra layer of security through Microsoft Entra ID (formerly Azure AD) prevents unauthorized access even if passwords are compromised. Enforcing MFA for admins and sensitive data access strengthens defense.
- Audit Logging and Monitoring: Enable audit trails to track changes, log access attempts, and detect anomalies. This improves compliance and facilitates investigations when security incidents arise.
- Client Secret Expiry Management: For integrations with external tools, use short-lived client secrets or certificates with expiration policies under 12 months. Regularly updating credentials reduces the risk of exposure.
- Data Protection and Encryption: Dynamics 365 uses Microsoft-managed encryption for data at rest and in transit. Organizations should also implement data loss prevention (DLP) policies to restrict unauthorized exports and sharing.
- Third-Party Integration Security: OAuth-based authentication, tokenized data transfers, and granular API permissions prevent data leaks when integrating Dynamics 365 with external tools like Power BI, SAP, and DocuSign.
- Compliance and Regulatory Adherence: Microsoft’s security framework aligns with industry standards (ISO 27018, GDPR, HIPAA). Organizations must ensure they manage user access, honor data subject requests (DSRs), and document security policies.
Conclusion
CRM security and compliance are essential for protecting customer data, maintaining trust, and adhering to global regulations like GDPR, CCPA, PIPEDA, and LGPD. Strong data governance and privacy measures reduce legal risks and enhance business credibility. At Nalashaa Digital, as a Dynamics 365 service provider, we help businesses implement robust security and compliance frameworks within their CRM systems to ensure data integrity and regulatory adherence.
Frequently Asked Questions
Access the Security Configuration Tool:
Navigate to System Administration > Security > Security Configuration in Dynamics 365.
Create a New Role:
Select the Roles tab. Click "Create new" to create a brand-new role. (Alternatively, you can duplicate an existing role and modify it.) Enter a unique name for the role.
Assign Duties to the Role:
Highlight the newly created role. Click the "Duties" tab. Click "Add references" to assign out-of-the-box (OOTB) or custom duties. Adding a duty also adds the associated privileges.
Modify Duties or Privileges (If Needed):
Do not remove privileges directly from OOTB duties, as this will impact all roles using that duty. Instead, duplicate the duty, modify it, and assign it to the role.
Publish the Changes:
Click "Publish" in the Security Configuration Tool to apply the changes.
Export and Import Custom Roles (Optional):
Once the role is configured, export it as a data file for use in other environments. After importing, publish the data entities to apply changes.
By default, Dynamics 365 does not provide an option to export security role permissions. However, you can use XrmToolBox with the "Export Security Role" plugin to simplify the process.
Steps to Export Security Roles:
- Download and install XrmToolBox from the XrmToolBox Website..
- Install the "Export Security Role" plugin from the plugin store.
- Connect to your Dynamics 365 organization within XrmToolBox.
- Open the "Export Security Role" plugin and click "Retrieve Roles" to load all security roles.
- Select the required security role to view its privileges and permissions.
- Use the search box to find specific entity permissions if needed.
- Click "Export" to generate an Excel file containing the security role's privileges.
Field-level security (now called column-level security) allows administrators to restrict access to specific fields within records.
Steps to Create Field-Level Security:
Enable Field-Level Security for a Field:
- Go to Advanced Settings > Customizations > Customize the System.
- Select the entity > Fields and choose the field to secure.
- Enable Field Security and Save & Publish changes.
Create a Field Security Profile:
- Navigate to Advanced Settings > Security > Field Security Profiles.
- Click "New," enter a profile name, and save it.
Define Permissions:
- Under Field Permissions, select the field and click "Edit."
- Assign Read, Create, or Update permissions based on requirements.
- Save the changes.
Assign Users or Teams:
- In the Field Security Profile, go to Users/Teams.
- Click "Add" and select users or teams to apply the permissions.
- Save and close.
Security roles in Dynamics 365 control user access to data and system functions. Users must have at least one role to perform tasks beyond basic capabilities. Roles can be automatically or manually assigned based on business needs.
Automatic Role Assignment:
- Configure rules in System Administration > Security > Assign Users to Roles to assign roles based on conditions.
- Run the assignment and review assigned roles under "Users."
Excluding Users from Auto Assignment:
- Manually exclude users from role assignment by selecting "Exclude from Role" in the security settings.
Manual Role Assignment:
- Navigate to Security > Assign Users to Roles, select a role, and manually add users.
- This role must be removed manually if needed.
Removing Users from Roles:
- Select a role, find the user, and click "Remove" to revoke access.
Recent Posts

Customer Service Module in Dynamics 365: A Complete Guide
Oct 18, 2023

Dynamics AX 2012 End of Life: Time to Transition to Dynamics 365 (F&SCM) Now
Oct 17, 2023

Serving customers the Dynamics way
Feb 05, 2020
Category
Our Expertise
About Author

Aiswarya Madhu
Aiswarya Madhu is an experienced content writer with extensive expertise in Microsoft Dynamics 365 and related Microsoft technologies. With over four years of experience in the technology domain, she has developed a deep understanding of Dynamics 365 applications, licensing, integrations, and their role in driving digital transformation for organizations across industries.
Never Miss News
Want to implement Dynamics 365?
We have plans which will meet your needs, and if not we can tweak them around a bit too!


